Certification Authority Authorization (CAA) records are a security policy used by DNS Administrators in order to let Certificate Authorities (CAs) know who is allowed to issue SSL certificates for that particular domain. The idea was drafted in January 2013. If you would like to learn more about CAA records, you can view the entirety of RFC 6844 here. This guide will walk you through creating CAA records inside of your No-IP account.
How to Add CAA Records
Who can use this CAA Record Guide?
This guide will walk you through creating CAA records inside of your No-IP account. If you use a different service for DNS management, the general steps should be similar, but not identical.
Step 1: Access Your DNS Service
Log into your No-IP account.
Step 2: Open “DNS Records”
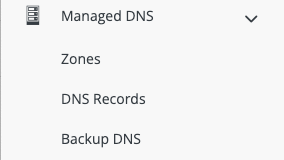
On the left side, click on Managed DNS and then DNS Records.
Step 3: Modify Your Domain
Click on Add Record to the right of your domain you wish to add the CAA record to.
Step 4: Select the CAA Record Option
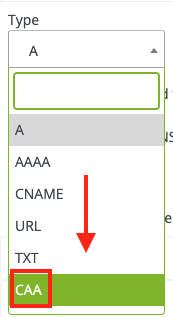
Click the field under Type which should open a drop down menu where you can select the CAA record option.
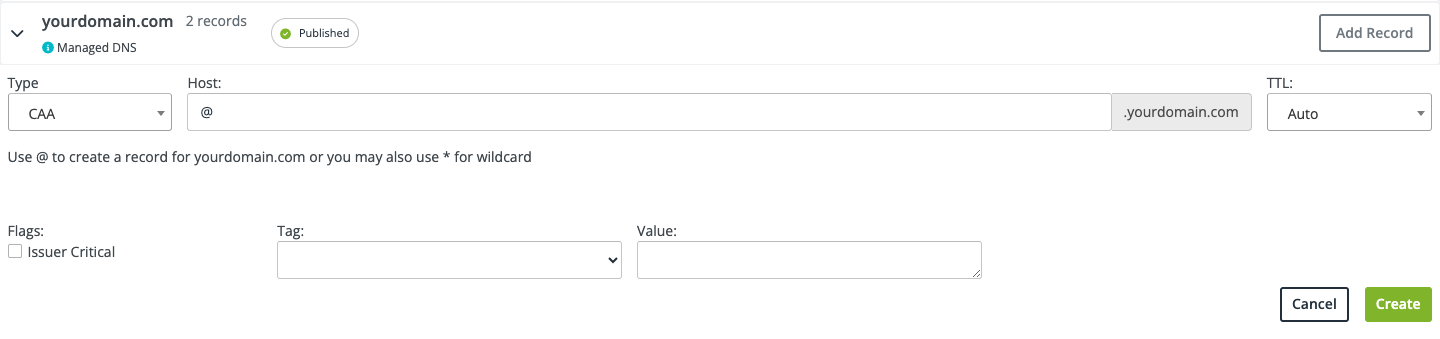
It should change the box to so that you can create your record. If this record is to be set on the root (apex) domain, you can enter “@” in the Host field.
Step 5: Set Your CAA Record’s Flags, Tags, and Value
There are three options to edit:
• Flags
• Tag
• Value
Flags
Flags is mostly for future usage of CAA records. When checked, the record is designated as Critical Flag. This means that if you have the flagged unchecked, any unrecognized tags in your record will be ignored and other requests will be processed. If it checked, then any unrecognized tags will halt the certificate issuance (assuming the issuer is Standards Compliant).
Tags
Tags offer five different options – Issue, issuewild, iodef, contactemail and contactphone. Using issue authorizes the CA to issue a certificate to that specific hostname the CAA record is on. If you need to authorize multiple hostnames, you will need to add a CAA record to each host. Using issuewild authorizes the CA to create a wildcard certificate (and only a wildcard cert) for that specific hostname the CAA record is on. Again, If you need to authorize multiple hostnames, you will need to add a CAA record to each host. Using iodef defines where people can send policy violation reports. Contactemail and contactphone are optional properties that can be included in the CAA record to facilitate communication to CA, allowing CA to reach out to domain owners should there be an issue with issuing certificates.
Value
Value is where you designate which CA is allowed to issue certificates for your domain/hostname.
Step 6: Save Your CAA Record
Once you are done setting your Flag, Tag, and Value, click Create to complete the process. Here are some examples and what they do:
This example shows a basic CAA record which will allow LetsEncrypt to issue SSL certificates example.com

This example shows a CAA record that establishes where policy violations should be mailed to: